Photo: Untitled, by Mike Donald

Untitled
© Sophie Beach for China Digital Times (CDT), get_post_time('Y'). |
Permalink |
No comment |
Add to
del.icio.us
Post tags: Mike Donald
Download Tools to Circumvent the Great Firewall


 Bloomberg Story Under Fire; Supply Chain Fears Remain
Bloomberg Story Under Fire; Supply Chain Fears Remain
Late last week, Bloomberg’s Jordan Robertson and Michael Riley published stunning claims that computer servers at nearly 30 American companies including Apple and Amazon had been compromised at the hardware level by Chinese manufacturers operating under official instructions. No consumer hardware is alleged to have been affected. While security experts have long warned of such vulnerabilities, the Bloomberg story has faced flat denials from companies involved, with British and American intelligence agencies speaking out to support them, and other observers raising an array of technical and other objections. From the original report:
There are two ways for spies to alter the guts of computer equipment. One, known as interdiction, consists of manipulating devices as they’re in transit from manufacturer to customer. This approach is favored by U.S. spy agencies, according to documents leaked by former National Security Agency contractor Edward Snowden. The other method involves seeding changes from the very beginning.
One country in particular has an advantage executing this kind of attack: China, which by some estimates makes 75 percent of the world’s mobile phones and 90 percent of its PCs. Still, to actually accomplish a seeding attack would mean developing a deep understanding of a product’s design, manipulating components at the factory, and ensuring that the doctored devices made it through the global logistics chain to the desired location—a feat akin to throwing a stick in the Yangtze River upstream from Shanghai and ensuring that it washes ashore in Seattle. “Having a well-done, nation-state-level hardware implant surface would be like witnessing a unicorn jumping over a rainbow,” says Joe Grand, a hardware hacker and the founder of Grand Idea Studio Inc. “Hardware is just so far off the radar, it’s almost treated like black magic.”
[…] The companies’ denials are countered by six current and former senior national security officials, who—in conversations that began during the Obama administration and continued under the Trump administration—detailed the discovery of the chips and the government’s investigation. One of those officials and two people inside AWS provided extensive information on how the attack played out at Elemental and Amazon; the official and one of the insiders also described Amazon’s cooperation with the government investigation. In addition to the three Apple insiders, four of the six U.S. officials confirmed that Apple was a victim. In all, 17 people confirmed the manipulation of Supermicro’s hardware and other elements of the attacks. The sources were granted anonymity because of the sensitive, and in some cases classified, nature of the information. [Source]
Supply chain integrity fears recently arose around the Chinese manufacturer of Google-branded security key hardware.
Bloomberg followed up this week with a second report alleging the discovery of compromised Ethernet ports on Supermicro servers by an unidentified "major U.S. telecommunications company," this time citing a named source, former Israeli intelligence officer Yossi Appleboum.
A major U.S. telecommunications company discovered manipulated hardware from Super Micro Computer Inc. in its network and removed it in August, fresh evidence of tampering in China of critical technology components bound for the U.S., according to a security expert working for the telecom company.
[…] The executive said he has seen similar manipulations of different vendors’ computer hardware made by contractors in China, not just products from Supermicro. “Supermicro is a victim — so is everyone else,” he said. Appleboum said his concern is that there are countless points in the supply chain in China where manipulations can be introduced, and deducing them can in many cases be impossible. “That’s the problem with the Chinese supply chain,” he said.
[…] The more recent manipulation is different from the one described in the Bloomberg Businessweek report last week, but it shares key characteristics: They’re both designed to give attackers invisible access to data on a computer network in which the server is installed; and the alterations were found to have been made at the factory as the motherboard was being produced by a Supermicro subcontractor in China. [Source]
The first report included denials from both Amazon Web Services and Apple, two of the nearly thirty American companies said to have been affected. Bloomberg posted the companies’ statements in full, separately, together with others from SuperMicro and China’s Ministry of Foreign Affairs. From Apple’s statement:
It’s untrue that AWS knew about a supply chain compromise, an issue with malicious chips, or hardware modifications when acquiring Elemental. It’s also untrue that AWS knew about servers containing malicious chips or modifications in data centers based in China, or that AWS worked with the FBI to investigate or provide data about malicious hardware. [Source]
From Amazon’s:
Over the course of the past year, Bloomberg has contacted us multiple times with claims, sometimes vague and sometimes elaborate, of an alleged security incident at Apple. Each time, we have conducted rigorous internal investigations based on their inquiries and each time we have found absolutely no evidence to support any of them. We have repeatedly and consistently offered factual responses, on the record, refuting virtually every aspect of Bloomberg’s story relating to Apple.
On this we can be very clear: Apple has never found malicious chips, “hardware manipulations” or vulnerabilities purposely planted in any server. Apple never had any contact with the FBI or any other agency about such an incident. We are not aware of any investigation by the FBI, nor are our contacts in law enforcement. [Source]
Both companies quickly followed up with further disavowals after the first article’s publication. Apple then tripled down with a letter to the Senate and House commerce committees from its Vice President for Information Security stating that “Apple’s proprietary security tools are continuously scanning for precisely this kind of outbound traffic, as it indicates the existence of malware or other malicious activity. Nothing was ever found.”
The bluntness and falsifiability of Apple’s denials, in particular, struck many observers. Apple blogger John Gruber alluded to the company’s frequent policy of declining to comment on news stories, writing that "in my experience, Apple PR does not lie. Do they spin the truth in ways that favor the company? Of course. That’s their job. But they don’t lie [….] They’d say nothing before they’d lie."
Technology journalist Kim Zetter commented:
David Vladeck, former head of the Federal Trade Commission’s Bureau of Consumer Protection, noted the potential costs of a dishonest denial in an email to Axios, saying that "the companies [would] risk enforcement by the FTC for engaging in a deceptive act that is likely to harm consumers. […] I am strongly disinclined to think they are lying.”
Reuters’ Guy Faulconbridge and Joseph Menn also reported a denial by Apple’s former chief lawyer:
Apple’s recently retired general counsel, Bruce Sewell, told Reuters he called the FBI’s then-general counsel James Baker last year after being told by Bloomberg of an open investigation into Super Micro Computer Inc , a hardware maker whose products Bloomberg said were implanted with malicious Chinese chips.
“I got on the phone with him personally and said, ‘Do you know anything about this?,” Sewell said of his conversation with Baker. “He said, ‘I’ve never heard of this, but give me 24 hours to make sure.’ He called me back 24 hours later and said ‘Nobody here knows what this story is about.’”
Baker and the FBI declined to comment Friday. [Source]
The report noted that the National Cyber Security Centre at British signals intelligence agency GCHQ had commented that, "We are aware of the media reports but at this stage have no reason to doubt the detailed assessments made by [Amazon Web Services] and Apple." The U.S. Department of Homeland Security issued a similar statement on Saturday. Bloomberg responded that the DHS would not necessarily be familiar with the content of a heavily siloed FBI counterintelligence investigation. Nevertheless, the DHS statement was the last straw for some observers. Johns Hopkins’ Thomas Rid tweeted that he was "filing the ‘Chinese hardware hack’ as a hoax until further notice," adding that "Bloomberg’s credibility on infosec stories is seriously damaged by now. An official reaction would be in order imho." Security expert "The Grugq" advised followers to “put a fork in it.”
Further blows followed. On Wednesday, the NSA’s Dan Joyce, who returned to the agency earlier this year after a stint as a White House cybersecurity adviser, told Dustin Volz at The Wall Street Journal that he had also been able to find corroboration despite his wide-ranging access:
In further comments from Politico, quoted at 9to5Mac, Joyce said that "I’ve got all sorts of commercial industry freaking out and just losing their minds about this concern, and nobody’s found anything. … There’s no there there yet […] Those companies will ‘suffer a world of hurt’ if regulators later determine that they lied. [… I have] grave concerns about where this has taken us […] I worry that we’re chasing shadows right now. I worry about the distraction that it is causing."
FBI director Christopher Wray told the Senate Homeland Security Committee on Wednesday that “we have very specific policy that applies to us as law enforcement agencies to neither confirm nor deny the existence of an investigation,” adding that “I do want to be careful that my comment not be construed as inferring, or implying I should say, that there is an investigation. […] Be careful what you read in this context.”
A further blow came from the the Risky Business podcast, where one of the story’s named sources, Joe Fitzpatrick, expressed several reservations, describing technical details in the piece as "jumbled" and saying that details he had provided were presented out of context. Bloomberg’s account, he said, "doesn’t make sense because there are so many easier ways to do it. There are so many easier hardware ways to do it, there are software, there are firmware approaches, and the approach that you’re describing [is] not scalable, it’s not logical." (Host Patrick Gray, who had previously withdrawn an endorsement of the report after an independent source retracted its supporting statements, returned to "Bloomberg’s dumpster fire" and past record on information security at greater length in a later episode.)
At Ars Technica, Dan Goodin cited similar suggestions that tampering with hardware might simply be unnecessary when the same ends could be achieved more easily and economically in software, with lower risk of discovery.
“Attackers tend to prefer the lowest-hanging fruit that gets them the best access for the longest period of time,” Steve Lord, a researcher specializing in hardware hacking and co-founder of UK conference 44CON, told me. “Hardware attacks could provide very long lifetimes but are very high up the tree in terms of cost to implement.”
He continued:
Once discovered, such an attack would be burned for every affected board as people would replace them. Additionally, such a backdoor would have to be very carefully designed to work regardless of future (legit) system firmware upgrades, as the implant could cause damage to a system, which in turn would lead to a loss of capability and possible discovery.
[…] Lord was one of several researchers who unearthed a variety of serious vulnerabilities and weaknesses in Supermicro motherboard firmware (PDF) in 2013 and 2014. This time frame closely aligns with the 2014 to 2015 hardware attacks Bloomberg reported. Chief among the Supermicro weaknesses, the firmware update process didn’t use digital signing to ensure only authorized versions were installed. The failure to offer such a basic safeguard would have made it easy for attackers to install malicious firmware on Supermicro motherboards that would have done the same things Bloomberg says the hardware implants did.
[…] “I spoke with Jordan a few months ago,” [security firm Rapid7’s chief research officer HD] Moore said, referring to Jordan Robertson, one of two reporters whose names appears on the Bloomberg articles. “We chatted about a bunch of things, but I pushed back on the idea that it would be practical to backdoor Supermicro BMCs with hardware, as it is still trivial to do so in software. It would be really silly for someone to add a chip when even a non-subtle change to the flashed firmware would be sufficient.” [Source]
At Serve The Home, Patrick Kennedy raised yet another objection:
[…] Supermicro servers are procured for US Military contracts and use to this day. Supermicro’s government business is nowhere near a large as some other vendors, but there are solutions providers who sell Supermicro platforms into highly sensitive government programs.
If the FBI, or other intelligence officials, had reason to believe Supermicro hardware was compromised, then we would expect it would have taken less than a few years for this procurement to stop.
Assuming the Bloomberg story is accurate, that means that the US intelligence community, during a period spanning two administrations, saw a foreign threat and allowed that threat to infiltrate the US military. If the story is untrue, or incorrect on its technical merits, then it would make sense that Supermicro gear is being used by the US military. [Source]
Meanwhile, the named source for the second Bloomberg report, Yossi Appleboum, told Kennedy that he felt the article had overemphasized the importance of Supermicro in what he described as a far broader problem.
I think [Supermicro] are innocent and someone is using them to dilute the story instead of mitigating the threat. Please help me, them, and everyone else to understand that the problem is bigger. Dealing with this as a Supermicro problem will ruin the opportunity to face the reality that we need to fix it.
[…] I want to be quoted. I am angry and I am nervous and I hate what happened to the story. Everyone misses the main issue. [Source]
Even before the tide had turned against Bloomberg’s report, many had commented that "if it is completely false, it is still a pretty big deal" given the gravity of the theoretical threat and the context of chilling U.S.-China relations and mounting security concerns over Chinese technology abroad. Ian Bogost elaborated on this theme at The Atlantic:
Who is right is a matter of corporate and national security. The exploits and hacks that have rocked the tech industry in recent years would seem minor compared with a foreign state gaining stealth access to the entire networks of companies and government agencies that manage enormous volumes of sensitive information. But even if the situation turns out to be different than Businessweek’s report, the scenario outlined in the piece (or one like it) is totally plausible. That plausibility, made newly visible, could combine with an accelerant: A tough American stance on Chinese business, including President Trump’s love for tariffs and trade war, and China’s increased dedication to independence. The resulting blaze has serious implications for the American technology business, and it won’t soon burn out.
[…] Whether or not a microcontroller backdoor turns out to have been installed somewhere in the Chinese supply chain, the conditions are right for anxiety about that possibility to impact U.S. trade with China in the high-tech industry. The truth of Bloomberg Businessweek’s investigation might matter less than the concerns it opens, or the open worries it further irritates—at the White House, at U.S. regulating bodies, and among the general public.
[…] If China begins to believe that its local manufacturing capabilities will outstrip its reliance on U.S. design, parts, and materials, then the risk associated with hardware-level attacks will lower considerably, while providing substantial benefit in the form of industrial or state espionage. Soon enough, as people start tearing down the Super Micro motherboards at the heart of the scandal, the world will learn whether the hack is a real crisis or a false alarm. But in some ways, it is a real crisis no matter the outcome. [Source]
George Washington University’s Henry Farrell and Georgetown University’s Abraham Newman examined the political implications of supply chain threats immediately after the Bloomberg report’s publication at The Washington Post:
Our academic research explores how countries are increasingly starting to weaponize interdependence — using these vulnerabilities and choke points for strategic advantage. China’s hacking of motherboards is a perfect example of this. As the Bloomberg article recounts, Chinese manufacturers dominate key aspects of computer hardware manufacturing. While some people had been confident that China would never hack exported components en masse — for fear of the damage that it would do to the Chinese economy — the Bloomberg article suggests that they have succumbed to temptation. It should be noted that the United States, too, has used its economic weight against Chinese hardware manufacturers. At one point the United States threatened the Chinese telecommunications giant ZTE with economic sanctions that would have made it impossible to buy chips from manufacturers with exposure to U.S. markets, a move that would effectively have driven ZTE out of business.
If the Bloomberg report is confirmed — and especially if it is one particular example of a broader problem — there will be very big economic repercussions. The U.S. economy and China’s economy are deeply interdependent. If the U.S. believes that Chinese firms are using this interdependence strategically to compromise U.S. technology systems with hardware components that undermine security, there will be pressure on the United States to systematically disengage from China and, perhaps, from global supply chains more generally.
This could have substantial knock-on repercussions for international trade, leading eventually to a world in which countries are much less willing to outsource components of sensitive systems to foreign manufacturers. Because we live in a world where technology is becoming ever more connected and ever more exploitable, this might mean that large swaths of the global economy are pulled back again behind national borders. The United States is already highly suspicious of Chinese telecommunications manufacturers, while organizations closely linked to U.S. intelligence are calling for a far more systematic reappraisal of the security implications of supply chains. In an extreme scenario, it may be that the globalized economy of the 1990s and 2000s was a brief aberration, which will be replaced by more constrained and limited international exchange between economies that keep the important parts of their manufacturing economy at home. [Source]
Security expert Bruce Schneier commented briefly on the issue of supply chain security on his blog:
I’ve written (alternate link) this threat more generally. Supply-chain security is an insurmountably hard problem. Our IT industry is inexorably international, and anyone involved in the process can subvert the security of the end product. No one wants to even think about a US-only anything; prices would multiply many times over.
We cannot trust anyone, yet we have no choice but to trust everyone. No one is ready for the costs that solving this would entail.
[…] Bottom line is that we still don’t know [whether Bloomberg’s reporting was accurate]. I think that precisely exemplifies the greater problem. [Source]
In a subsequent post on the second Bloomberg report, he expressed less confidence than many others in the significance of the various denials, maintaining that "the story is plausible. The denials are about what you’d expect."
Fellow security expert Brian Krebs argued similarly in a longer exploration of supply chain threats on his own blog:
[…] Even if you identify which technology vendors are guilty of supply-chain hacks, it can be difficult to enforce their banishment from the procurement chain. One reason is that it is often tough to tell from the brand name of a given gizmo who actually makes all the multifarious components that go into any one electronic device sold today.
[… T]he issue here isn’t that we can’t trust technology products made in China. Indeed there are numerous examples of other countries — including the United States and its allies — slipping their own “backdoors” into hardware and software products.
Like it or not, the vast majority of electronics are made in China, and this is unlikely to change anytime soon. The central issue is that we don’t have any other choice right now. The reason is that by nearly all accounts it would be punishingly expensive to replicate that manufacturing process here in the United States. [Source]
The New York Times’ Paul Mozur wrote on Friday that suspicion over supply chain security runs both ways between China and the U.S.:
After Edward J. Snowden’s disclosures about how the United States used American companies to spy overseas, China accelerated a campaign to build just about every piece of advanced tech itself. That quest for self-reliance led it to introduce quotas on foreign-made products and require so-called tech transfers for market access. Those policies helped pave the way to the current trade war between the United States and China.
Not surprisingly, the United States has had the same spying concerns as China. Congress effectively blocked China’s Huawei and ZTE from selling their equipment to major telecom carriers in the United States in 2012, and more recently made it harder for Huawei to sell phones.
The fact that the two sides share the same fears shows how difficult it can be to ensure security in a world in which the design, production and assembly of electronics occur across multiple countries.
[…] Neither side is happy with this. Both China and the United States will probably continue to winnow their mutual tech reliance. It won’t be easy. They are working against 40 years of economic integration and a tremendously complex web of big and small companies. [Source]
Meanwhile, a number of other reports have suggested that Chinese economic espionage is resurging after abating in the wake of an agreement secured by the Obama administration in 2015. (The first Bloomberg report described "the White House’s deep concern that China was willing to offer this concession because it was already developing far more advanced and surreptitious forms of hacking founded on its near monopoly of the technology supply chain.") Reuters’ Christopher Bing reported last week, before the Bloomberg article’s publication:
The U.S. government on Wednesday warned that a hacking group widely known as cloudhopper, which Western cybersecurity firms have linked to the Chinese government, has launched attacks on technology service providers in a campaign to steal data from their clients.
The Department of Homeland issued a technical alert for cloudhopper, which it said was engaged in cyber espionage and theft of intellectual property, after experts with two prominent U.S. cybersecurity companies warned earlier this week that Chinese hacking activity has surged amid the escalating trade war between Washington and Beijing.
[…] “I can tell you now unfortunately the Chinese are back,” Dmitri Alperovitch, chief technology officer of U.S. cybersecurity firm CrowdStrike, said Tuesday at a security conference in Washington, D.C.
“We’ve seen a huge pickup in activity over the past year and a half. Nowadays they are the most predominant threat actors we see threatening institutions all over this country and western Europe,” he said.
Analysts with FireEye, another U.S. cybersecurity firm, said that some of the Chinese hacking groups it tracks have become more active in recent months. [Source]
China’s Foreign Ministry has pushed back against these claims:
[Spokesperson Lu Kang] said it is "purely out of ulterior motive that some companies and individuals in the US use so-called cyber theft to blame China for no reason."
"China is one of the main victims of cyber theft and attacks, and a staunch defender of cyber security. China has always firmly opposed to and fought against any forms of cyber attacks and theft," said Lu during a regular press conference.
"According to documents revealed by (US National Security Agency whistleblower) Edward Snowden and others, the international community has long been aware which country had carried out large-scale long-term surveillance of foreign governments, enterprises, and individuals, and who is the world’s largest cyber attacker," he added. [Source]
At Politico EU, however, Laurens Cerulus reported similar concerns from Europe:
The European Commission Thursday met a group of national government experts, foreign affairs officials and industry lobbyists to go over a study by PricewaterhouseCoopers and the Commission department that is likely to lead to EU action in coming months.
The study, an executive summary of which was obtained by POLITICO, offers a peek into “public and private sector concerns about the increasing risks associated with cyber-theft of trade secrets in Europe.”
In the manufacturing sector, it said, industrial espionage and cybertheft of trade secrets constitute up to 94 percent of all cyberattacks. The summary cites estimates that cyber espionage is costing Europe up to €60 billion in economic growth — a figure that would rise as European companies digitize their services.
[…] Europe’s largest business lobby BusinessEurope released a statement Thursday in which it asks the EU to come up with a “strategy to deter hostile actors” like China. “Diplomatic action or economic retaliation could be considered,” the group says, adding that “the EU could seek to cooperate with the United States, Japan and other OECD economies to apply political pressure.” [Source]
On Wednesday, The Washington Post’s Ellen Nakashima reported the possibly unprecedented extradition of a Chinese intelligence officer for stealing commercial secrets:
Yanjun Xu, a senior officer with China’s Ministry of State Security (MSS), is accused of seeking to steal trade secrets from leading aviation firms, top Justice Department officials said. His capture helps vindicate law enforcement officials who have faced criticism in recent years that indictments of foreign operatives are unlikely to result in the defendants setting foot in a courtroom.
Current and former officials said Xu’s extradition is apparently the first time a Chinese government spy has been brought to the United States to face charges.
[…] Justice Department officials said the indictment is the latest example of China seeking to develop its economy at the expense of American firms and know-how. Though China has often used computer hacking to filch secrets, this case relied on traditional espionage techniques, including the attempted recruitment of corporate insiders.
[…] “If not the first, this is an exceptionally rare achievement — that you’re able to catch an espionage operative and have them extradited to the United States,” said John Carlin, a former assistant attorney general for national security. “It significantly raises the stakes for China and is a part of the deterrence program that some people thought would never be possible.” [Source]
At The New York Times, meanwhile, the Council on Foreign Relations’ Adam Segal assessed the risk of covert online Chinese interference in American politics, following accusations of such from the White House. (Read more on these claims from Brian Barrett at Wired, James Palmer at Foreign Policy, and CDT.)
Neither the president nor the vice president charged China with stealing and releasing politically sensitive emails or manipulating social media, as the Russian government appears to have done to sway the 2016 presidential election.
And the Chinese government has not yet tried to use cyberspace to disrupt American elections, it seems. Yet the threat is real.
China has both the playbook and the capacity to interfere. Chinese entities operating with the assent of the government in Beijing already have mounted long-running cyberespionage campaigns against United States government agencies, the defense industry and American private companies. And they have conducted disruptive cyberattacks on political processes and social media campaigns in targets the Chinese government considers internal: Tibet, Hong Kong and Taiwan.
[…] As it watches Washington struggle to find a coherent response to Russian interference in 2016, the Chinese government is likely to think that it could avoid serious repercussions if it ever launched similar cyberattacks in the United States. Were China’s strategic calculations to change, there would be little to stop it from entering the online fray. [Source]
© Samuel Wade for China Digital Times (CDT), get_post_time('Y'). |
Permalink |
No comment |
Add to
del.icio.us
Post tags: Amazon, Apple, Bloomberg, cyberespionage, cybersecurity, digital security, fbi, manufacturing, NSA, snowd, supply chain
Download Tools to Circumvent the Great Firewall


 Minitrue: Share the Following Articles on China-U.S. Relations
Minitrue: Share the Following Articles on China-U.S. Relations
The following propaganda instructions, issued to the media by government authorities, have been leaked and distributed online.
Dengfeng City Network Information Office: Urgent Notice: All personnel take immediate action to share the following articles via WeChat and Weibo. The deadline is 3:30 pm. This forwarding and commenting task is to be included in the year-end assessment. Please actively share, provide commentary, and forward the screenshot to your groups. (October 10) [Chinese]
This order was issued to promote the circulation of two articles about U.S.-China relations and China’s role in the global order as tit-for-tat tariffs escalated an ongoing trade war between the two countries. The first article is from Xinhua and is titled “Accounting for China’s Contributions to the World”; below is an excerpt translated by CDT:
Some American politicians have described Chinese growth as “driven by U.S. investment in China.” This is not at all true; rather, it is that over one billion Chinese people worked hard. Even when it comes to investing in China, whether it is the flow rate or level of capital stock, the U.S. is not the largest player, let alone the one that “reconstructed China.” According to relevant statistics, since the 1980s, U.S. investment in China has only accounted for about seven to ten percent of foreign investment. On the contrary, the U.S. has made boatloads of money from Chinese investment. [Source]
The second article is titled “The General Downhill Trend of America Has Not Changed,” from Guangming Net; excerpts translated by CDT:
In terms of soft power, Trump has dealt a major blow to the image of the U.S. Trump is significantly stretching thin the international strategic reputation that had been accumulated by the U.S. over many years. This is also affecting allies’ strategic expectations and their interactions with the U.S. For example, after promulgating the “Indo-Pacific” strategy, India, Japan, Australia and other countries have had limited responses, while Sino-Indian and Sino-Japanese relations are actually in the midst of improving. Trump’s speech at the United Nations has been questioned, as the Washington Post admits, “Trump’s America is a bully, not a beacon.” Joseph Nye, the father of soft power, sharply criticized Trump as severely weakening the U.S.’ soft power and greatly reducing its attractiveness.
Chinese society wants to eradicate the “illness of fearing and worshipping the U.S.”
In 1938, Mao Zedong wrote his monumental work “On Protracted War” in the caves of northern Shaanxi. He criticized the “rapid victory” and “conquered nation” theories as fallacies, and like a shining light in the endless night, he brought 400 million Chinese to ultimate victory against the Japanese imperialist aggressors. Eighty years later, today’s China is incomparable to the China of the past. In the face of the “Trump offensive,” the descendants of the Yellow Emperor need not blame or belittle themselves, and we should especially not have extravagant hopes that “admitting fear” lets us beg for peace and pity. Of course, we should not be arrogant and conceited. China’s development has entered the “intensive cultivation period.” We are in the midst of transitioning from our past emphasis on “quantity” type growth to the high-quality development stage of “equally emphasizing quantity and quality.” As long as we persist in deepening reform and opening up to the outside world, especially via implementing policy programs to the fullest in some important areas, none of the U.S.’ attempts at containment will be able to interrupt China’s development. As long as China steadily moves forward in accordance with the pace of its own reform and development, and Chinese people become even more resolutely determined, confident, and united in willpower, they will be able to fight off the U.S.’ “bullying,” and realize the great rejuvenation of the Chinese nation. [Chinese]
An earlier propaganda directive from June outlined rules for coverage of trade conflicts with the U.S.
Translation by Lisbeth.
 Since directives are sometimes communicated orally to journalists and editors, who then leak them online, the wording published here may not be exact. Some instructions are issued by local authorities or to specific sectors, and may not apply universally across China. The date given may indicate when the directive was leaked, rather than when it was issued. CDT does its utmost to verify dates and wording, but also takes precautions to protect the source. See CDT’s collection of Directives from the Ministry of Truth since 2011.
Since directives are sometimes communicated orally to journalists and editors, who then leak them online, the wording published here may not be exact. Some instructions are issued by local authorities or to specific sectors, and may not apply universally across China. The date given may indicate when the directive was leaked, rather than when it was issued. CDT does its utmost to verify dates and wording, but also takes precautions to protect the source. See CDT’s collection of Directives from the Ministry of Truth since 2011.
© Sophie Beach for China Digital Times (CDT), get_post_time('Y'). |
Permalink |
No comment |
Add to
del.icio.us
Post tags: Directives from the Ministry of Truth, propaganda, tariffs, trade war, U.S trade, U.S. relations
Download Tools to Circumvent the Great Firewall


 Interpol’s Meng Hongwei ‘Under Investigation’
Interpol’s Meng Hongwei ‘Under Investigation’
Interpol said it had received his resignation “with immediate effect” late on Sunday. It was the latest twist in the mystery of Meng’s disappearance last month after he flew from France to China.
[…] On Sunday, a statement from China’s ruling Communist party said Meng was “under the monitoring and investigation” of the new anti-corruption unit, the National Supervision Commission, for suspected serious violations of state law. It gave no further information about the reason for his arrest and detention.
Meng, 64, who is also a senior Chinese security official, had more than 40 years’ experience in criminal justice, particularly in the field of drugs control, counter-terrorism, immigration and border control, before becoming president of Interpol, the international criminal police organisation based in Lyon, in November 2016. He is a senior member of the Communist party. [Source]
Laurie Chen and Catherine Wong at the South China Morning Post cited unnamed sources that Meng is currently under investigation on suspicion of unspecified legal violations, noting that he was “taken away” immediately upon arriving in China.
It is not yet clear why Meng is being investigated or exactly where he is being held.
[…] Under China’s supervision law, a suspect’s family and employer must be notified within 24 hours of a detention, except in cases where doing so would hinder an investigation. It appears Meng’s wife was not informed.
[…] While Meng is listed on the website of China’s Ministry of Public Security as a vice-minister, he lost his seat on its Communist Party Committee, its real decision-making body, in April.
According to his own page on the site, Meng’s last official engagement was on August 23, when he met Lai Chung Han, a second permanent secretary of Singapore. [Source]
China’s Central Commission for Discipline Inspection issued a one-line statement over the weekend corroborating the media’s account of the investigation, stating that Meng is on “suspicion of violating the law” and was “under the supervision” of the National Supervision Commission, China’s new anti-corruption body. It did not elaborate on why Meng is being investigated or where he is being held.
Although it is yet unclear what Meng is being investigated for, his case resembles the downfall of senior officials when they are suspected of graft, which often begins with removal from key roles within the party. While Meng is still officially listed as China’s vice-minister of public security, AFP journalist Matt Knight notes that Meng has been stripped of his Party Committee membership since April and removed from several other internal leadership positions since late last year.
If speculations hold true, Meng would be the latest senior official to be caught in President Xi Jinping’s high-profile crackdown on corruption within the Communist Party–one that has targeted more than one million officials at all levels of government and military bodies, from lowly “flies” to powerful “tigers.” Critics have argued that the ongoing campaign is being used as a weapon by Xi to take down political rivals and consolidate his power. Prominent politicians and military generals who have been netted in the anti-graft campaign thus far include former rising political star Sun Zhengcai, security chief Zhou Yongkang, and general Guo Boxiong. China’s minister of public security Zhao Kezhi was cited telling a group of senior police officials in Beijing that Meng was accused of taking bribes, among other crimes. It has also been hinted that Meng’s apparent downfall is likely in some ways connected to Zhou Yongkang. However, those close to Zhou have dismissed the speculation that the two cases are linked, citing that the two men were ‘never close.’
The National Supervision Commission (NSC) handling Meng’s case is a powerful investigatory body established earlier this year to oversee President Xi’s ongoing anti-corruption efforts. The agency is a strengthened version of the Central Commission for Discipline Inspection that functions independently of the courts and is authorized to hold suspects for months at a time without providing legal counsel. The agency operates a new detention system called “liuzhi,” which is likely what Meng is being put through. From Human Rights Watch’s Maya Wang:
This means it’s highly likely that Meng has been subjected to “liuzhi,” a form of secret detention effectively controlled by the Chinese Communist Party. Under liuzhi, detainees are held incommunicado – without access to lawyers or families – for up to six months.
Little is known about the treatment of detainees during liuzhi, because the program and the government agency running it, the National Supervision Commission, are new. In March this year the commission absorbed existing graft-fighting powers vested in other government departments, and was empowered to investigate anyone exercising public authority. It shares space and personnel with the Party’s disciplinary agency, the Central Commission for Disciplinary Inspection (CCDI).
[…] In its effort to give liuzhi a veneer of legality that shuanggui lacked, authorities say interrogations will be videotaped and families notified within 24 hours, among other reforms. But so far, the signs are not promising: in May, a 45-year-old man reportedly died after 26 days in liuzhi, his body covered in bruises.
What’s next for Meng Hongwei? The formula is simple: like others forcibly disappeared before him, including human rights activists mistreated in custody by Meng’s public security ministry, he faces detention until he confesses under duress, an unfair trial, and then harsh imprisonment, possibly for many years. While Meng’s whereabouts remain elusive, his fate is not. [Source]
The Chinese government’s announcement of Meng’s detention came shortly after Meng’s wife Grace revealed at a press conference in Lyon that she had received an ominous text message from her husband signalling he was in danger minutes before he disappeared. Citing safety concerns for herself and her children, Mrs. Meng kept her back to reporters while she made an emotional plea for international help in bringing her husband to safety. Her actions were unusual given that family members of disgraced Communist officials almost never make such public appeals. AP’s Gillian Wong and John Leicester report:
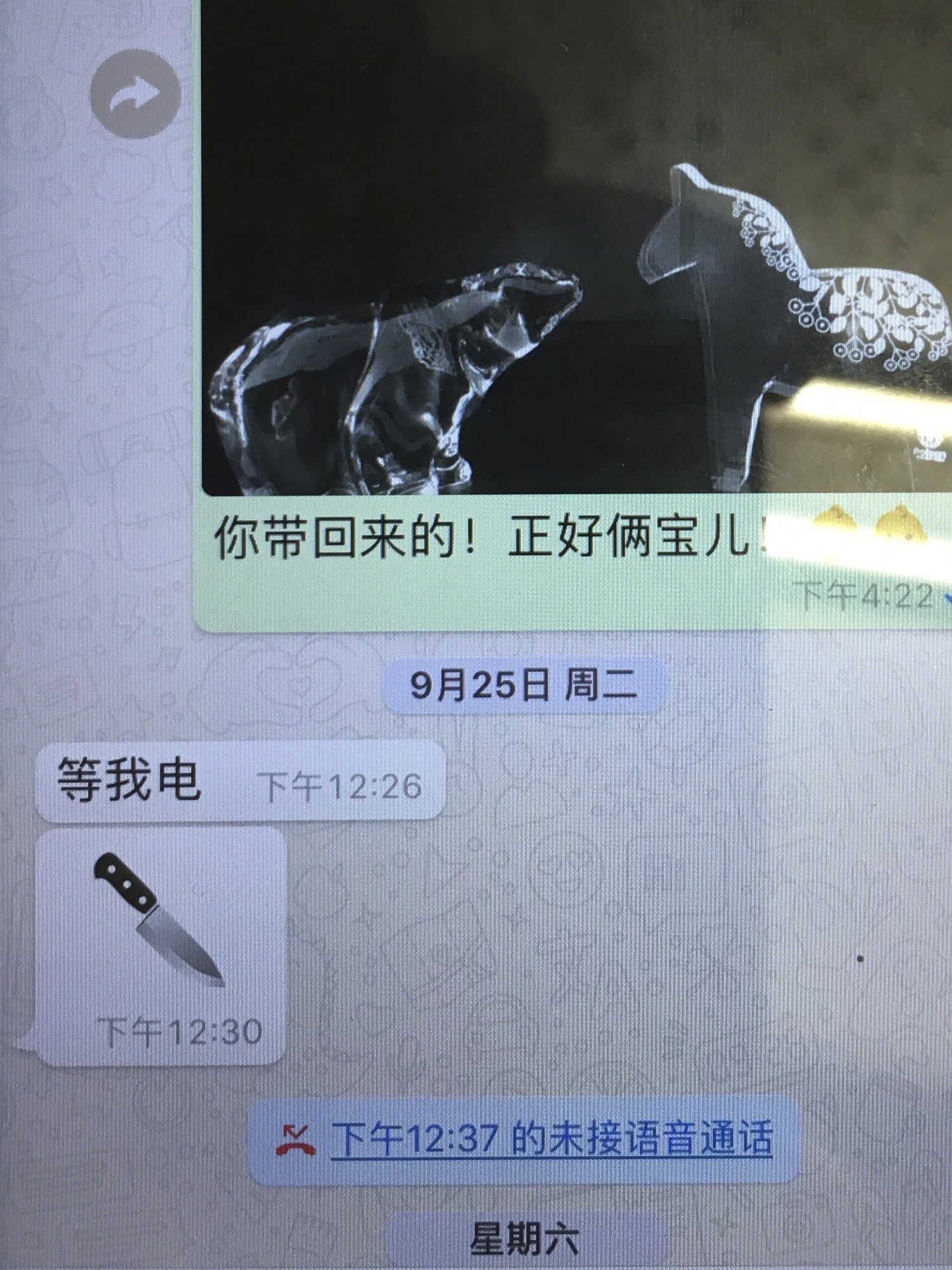
Grace Meng said she hadn’t heard from her husband since Sept. 25. Using his Interpol mobile phone, he sent her the emoji image of a kitchen knife that day, four minutes after he sent a message saying, “Wait for my call.”
[…] Of the knife image, she said: “I think he means he is in danger.” She said he was in China when he sent the image.
“This is the last, last message from my husband,” she said. “After that I have no call and he disappeared.”
She said he regularly traveled back and forth between Lyon and China for his job. He had been on a three-country tour, to Norway, Sweden and Serbia, for Interpol before his latest trip back to China, she said. [Source]
Mrs. Meng further revealed that she has been the target of online harassment and death threats. In a separate article, Gillian Wong and John Leicester detail a chilling call Mrs. Meng received from a man allegedly working on behalf of the Chinese government:
“You listen, but you don’t speak,” the man on the other end said. “We’ve come in two work teams, two work teams just for you.”
[…] Speaking to the AP late Monday at a hotel in Lyon, the French city where she lives and Interpol is based. Grace Meng said she had put their two boys to bed when she got the threatening call. It was one week after her last contact with her husband. On Sept, 25, he sent her from China an emoji of a knife — suggesting to her he was in danger.
The man who called her on her mobile phone spoke in Chinese, she said. She said the only clue he gave about his identity was saying that he used to work for Meng, suggesting that the man was part of China’s security apparatus. He also said he knew where she was.
“Just imagine: My husband was missing, my kids were asleep, all my other phones weren’t working, and that was the only call I got. I was so frightened,” she said. [Source]
China’s willingness to risk its international reputation and go after an official with high international standing sets a precedent for how far the Xi administration is willing to go to prioritize domestic politics and Party survival over respect for international norms. Meng’s arrest is expected to undermine China’s legitimacy as it seeks to play a greater role in international affairs, with many now left uncertain whether it remains sensible to continue giving China leadership roles in multilateral organizations. The New York Times’ Edward Wong and Alissa J. Rubin report:
Mr. Meng’s appointment “was considered quite an achievement for China and a sign of its international presence and growing influence,” said Julian Ku, a professor at Hofstra University’s Maurice A. Deane School of Law, who has studied China’s relationship with international law.
While China may have had its eye on placing its citizens in other top posts at prominent global organizations, “the fact that Meng was ‘disappeared’ without any notice to Interpol will undermine this Chinese global outreach effort,” Mr. Ku said. “It is hard to imagine another international organization feeling comfortable placing a Chinese national in charge without feeling nervous that this might happen.”
[…] His detention means that internal party dynamics supersede any concern from the party about international legitimacy or transparency.
The party’s moves in this case “suggest that the domestic considerations outweighed the international ones,” said Mr. Ku, the law professor. “This has always been true for China, but perhaps not so obviously true as in this case.” [Source]
The incident shows that internal party loyalty and obedience is of utmost importance in Xi’s China, irrespective of external pressure. Ben Westcott reports for CNN:
Unusually, the statement released by the Chinese government confirming Meng had been detained under suspicion of corruption didn’t just mention the charges. It also stressed the importance of loyalty to both Chinese President Xi Jinping and the Party’s leadership.
Michael Caster, human rights advocate with Safeguard Defenders, told CNN he found the wording of the Chinese statement “really alarming.”
“I think it’s very concerning (that) China thinks it can abduct and arbitrarily detain the sitting head of an international organization without serious consequences,” said Caster.
“Not only is it pointing out the supposed criminal violation, its … emphasizing that ultimately Meng Hongwei was serving at the discretion of the Communist Party, which is headed by Xi Jinping,” added Caster. [Source]
China Change has compiled a list of key takeaways from Meng’s arrest and how it fits into broader changes taking place in China:
We will refrain from wallowing in the rich irony and absurdity of the event, but there are a few points to register:
- People who hold positions in international organizations, regardless of their position or nationality, should perform their duties as independent individuals, rather than as representatives of their respective countries. But the Chinese Communist Party (CCP) affords none of its members such independence, Meng Hongwei among them. As far as the CCP is concerned, he is the Party’s man above all, and the Party can sanction him at any time as it sees fit, even during his Interpol term.
- It follows that Meng Hongwei, in his capacity as Interpol chief, was inevitably subject to the Party’s directives and control.
- Meng Hongwei’s mafia-style abduction sends a stark message to the international community: totalitarian China does not conform to international procedures and is incapable of participating in world affairs as a normal country.
- Almost exactly a year ago, Xi Jinping attended the 86th Interpol general assembly in Beijing and delivers a keynote speech emphasizing “cooperation, innovation, the rule of law and win-win results and build a universal and secure community of shared future for mankind.” [Source]
Ultimately, the Interpol incident could not only cost China its reputation and aspirations to lead global organizations but also hurt those international institutions themselves as they grapple with the now manifest political complications of appointing Chinese officials. From Adam Minter at Bloomberg:
But the impact of China’s power play will be even more far-reaching. Chinese participation in global organizations isn’t just a status-enhancing honor. It’s a necessity: Solving international problems of all sorts will be harder if the world’s second-largest economy doesn’t play a leading role in addressing them. If global institutions can no longer trust that Chinese domestic politics won’t interfere with their work — and feel secure appointing Chinese to top positions — their legitimacy and effectiveness will inevitably suffer.
Prior to Meng’s detention, the case for greater Chinese influence in such institutions seemed clear-cut. In the space of 40 years, China has evolved from economic, military and cultural afterthought into a juggernaut. As its status has grown, so has the ruling Communist Party’s desire to play a greater role in setting global standards. For years, the World Bank has been a particular focus, with Chinese leaders arguing that the institution’s voting structure didn’t sufficiently recognize China’s economic status or the voices of other developing countries. In 2016, the World Bank signaled its agreement by appointing Yang Shaolin, a Chinese national, to be its second-in-command.
[…] Yet by abducting him without any notice to Interpol (much less a public accounting of charges), China has clearly demonstrated its lack of respect for international standards of governance. The damage will be lasting. Global organizations will be understandably wary of putting another Chinese into a leadership position, and the Chinese government — rarely willing to admit a wrong — is unlikely to offer assurances that it will respect international norms in the future. That’s a setback for China, and a tragedy for international organizations that depend on global cooperation to manage or solve issues that impact us all. [Source]
© cindyliuwenxin for China Digital Times (CDT), get_post_time('Y'). |
Permalink |
No comment |
Add to
del.icio.us
Post tags: Central Commission for Discipline Inspection, discipline inspection, Interpol, law enforcement, Meng Hongwei, Xi anti-corruption campaign
Download Tools to Circumvent the Great Firewall


